1. What is Cybersecurity?
Cybersecurity means protecting computers, networks, devices, and data from hackers, viruses, and cybercriminals.
👉 Think of it as a digital shield.
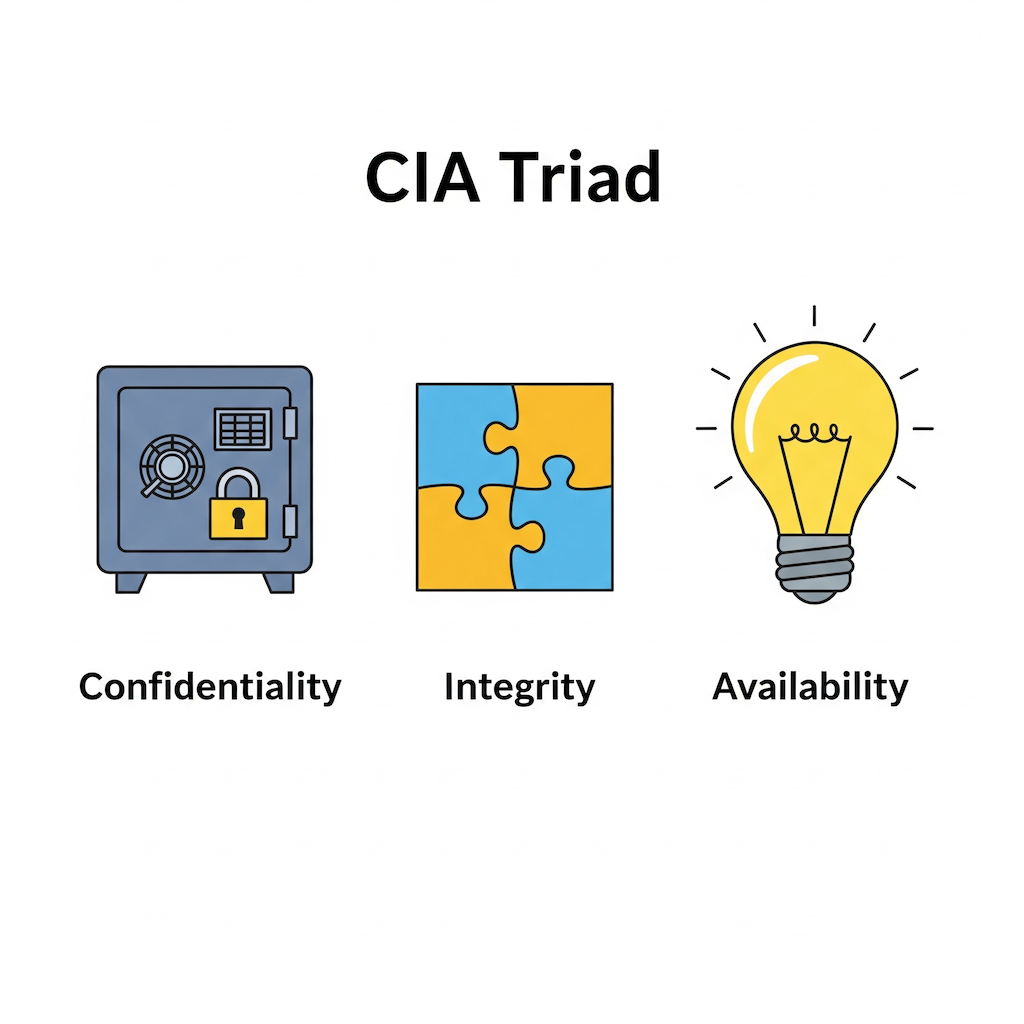
Goal = CIA Triad
- Confidentiality → Keep data private (only authorized people can see).
- Integrity → Keep data correct (not changed by anyone).
- Availability → Data/systems always available when needed.
2. Types of Cyber Threats
- Malware → Harmful software (virus, worm, trojan, ransomware, spyware).
- Phishing → Fake emails/messages to steal info (passwords, bank details).
- DoS/DDoS → Overloading servers to shut them down.
- MITM (Man-in-the-Middle) → Attacker secretly sits between two people’s communication.
- SQL Injection → Inserting malicious code into databases.
- Zero-Day Exploit → Attacking before a patch is released.
- Password Attacks → Guessing/cracking passwords.
3. Cybersecurity Measures (Defense Tools)
- Firewall → Blocks suspicious traffic.
- Antivirus → Detects and removes malware.
- Encryption → Turns data into secret code.
- MFA (Multi-Factor Authentication) → Extra security (password + OTP).
- Access Control → Limits who can access what.
- Regular Updates → Fix weaknesses.
- Security Awareness Training → Teach people safe practices.
4. Types of Hackers
- White Hat → Ethical hackers (good guys, test systems).
- Black Hat → Criminal hackers (steal/damage).
- Grey Hat → In-between (may find issues without permission, sometimes report).
- Script Kiddies → Use ready-made tools, no deep skills.
- Hacktivists → Hack for social/political causes.
- Insiders → Employees misusing access.
- Red Hat → Fight against black hats aggressively.
- Blue Hat → External testers hired before system launch.

5. Key Cybersecurity Terms
- Vulnerability → Weakness in system.
- Threat → Potential danger.
- Risk → Possibility of threat exploiting weakness.
- Attack → Actual attempt to exploit.
- Common Attacks:
- Virus, Worm, Trojan, Ransomware, Spyware, Adware, Rootkit, Botnet.
- Phishing (Email), Smishing (SMS), Vishing (Voice), Whaling (CEO target).
- DoS/DDoS, MITM, SQL Injection, XSS, Brute Force, Spoofing.
6. Cybersecurity Laws in India
Main Laws:
- IT Act, 2000 → Defines cybercrimes & punishments.
- Sec 43 → Unauthorized access.
- Sec 65 → Tampering with source code.
- Sec 66 → Hacking/identity theft.
- Sec 66F → Cyber terrorism (life imprisonment).
- Sec 69A → Govt. can block websites.
- Sec 70B → CERT-In (incident response agency).
- DPDPA, 2023 (Digital Personal Data Protection Act)
- Protects personal data.
- Consent required for data use.
- Companies must secure data & report breaches.
- Big fines for violations.
- CERT-In (Indian Computer Emergency Response Team) → Handles cybersecurity incidents.
International Standards:
- ISO 27001 → Global info security standard.
- NIST Framework → 5 steps → Identify, Protect, Detect, Respond, Recover.
- GDPR (EU law) → Strong data privacy rules.
7. Common Cybersecurity Tools
- Antivirus → Removes malware.
- Firewall → Blocks bad traffic.
- VPN → Safe encrypted internet connection.
- IDS/IPS → Detect/stop intrusions.
- SIEM → Collects & analyzes logs for threats.
- DLP → Stops data leaks.
- Pen Testing Tools → Kali Linux, Metasploit, Burp Suite.
- Wireshark → Network analysis.
8. Social Engineering Attacks (Human Tricks)
- Phishing → Fake emails.
- Spear Phishing → Targeted phishing.
- Whaling → Targets CEOs.
- Smishing → Fake SMS.
- Vishing → Fake phone calls.
- Pretexting → Fake story to steal info.
- Baiting → Free lure (USB, downloads).
- Quid Pro Quo → “Help” in exchange for info.
- Tailgating → Entering with authorized person.
- Shoulder Surfing → Watching someone’s screen/PIN.
9. Emerging Trends
- AI in Attacks & Defense (smart phishing, malware, AI detection).
- Ransomware-as-a-Service (RaaS) → Ransomware sold like service.
- Supply Chain Attacks → Hacking vendors to reach big targets.
- Cloud Security Risks → Misconfigurations, unauthorized access.
- IoT Weakness → Smart devices easy to hack.
- Quantum Threats → Future computers may break current encryption.
- Zero Trust Security → “Never trust, always verify.”
- Human Error → Still biggest cause of breaches.
10. Basic Security Practices (For Users)
✅ Use strong, unique passwords.
✅ Enable 2FA.
✅ Don’t click suspicious links.
✅ Keep software updated.
✅ Backup data regularly.
11. Cybersecurity Certifications (For Careers)
- CEH – Certified Ethical Hacker
- CISSP – Information Security Professional
- CompTIA Security+ – Beginner-friendly
- CISA – Information Systems Auditor
🔑 Quick Revision (Exam Cheatsheet)
- Threats → Malware, Phishing, DoS, MITM, SQL Injection.
- Defense → Firewall, Antivirus, Encryption, MFA, Updates.
- CIA Triad → Confidentiality, Integrity, Availability.
- Hackers → White, Black, Grey, Script Kiddies, Hacktivists.
- Tools → Wireshark, Kali Linux, Metasploit.
- Trends → AI, IoT, Cloud, Ransomware.
Cybersecurity – MCQ
. What is the primary objective of cybersecurity?
A. To increase internet speed
B. To protect systems, networks, and data from cyberattacks
C. To create complex algorithms for encryption
D. To train individuals on ethical hacking
Answer: B. To protect systems, networks, and data from cyberattacks
2. What does the “C” in the CIA triad stand for in cybersecurity?
A. Control
B. Cybersecurity
C. Confidentiality
D. Connection
Answer: C. Confidentiality
3. Which of the following is NOT a type of malware?
A. Worm
B. Phishing
C. Trojan
D. Ransomware
Answer: B. Phishing
4. What is phishing?
A. Encrypting files to make them inaccessible
B. A technique to manipulate users into revealing sensitive information
C. A way to redirect network traffic to fake websites
D. A virus that self-replicates
Answer: B. A technique to manipulate users into revealing sensitive information
5. What is the primary function of a firewall?
A. To create backup copies of data
B. To detect and remove malware
C. To filter incoming and outgoing network traffic
D. To encrypt data
Answer: C. To filter incoming and outgoing network traffic
6. Which of the following is a popular tool used for network analysis?
A. Metasploit
B. Wireshark
C. Kali Linux
D. Snort
Answer: B. Wireshark
7. What is the purpose of encryption in cybersecurity?
A. To speed up data transmission
B. To make data unreadable to unauthorized users
C. To eliminate viruses from a system
D. To compress data for storage
Answer: B. To make data unreadable to unauthorized users
8. Which of the following is an example of a Denial of Service (DoS) attack?
A. Intercepting data between two communicating devices
B. Overloading a server to make it unavailable
C. Installing malware on a system
D. Stealing login credentials
Answer: B. Overloading a server to make it unavailable
9. What is the No-Cloning Theorem in cybersecurity?
A. Data cannot be backed up multiple times
B. Quantum states cannot be exactly copied
C. Hackers cannot clone a network’s architecture
D. Files cannot be cloned without admin rights
Answer: B. Quantum states cannot be exactly copied
10. Which algorithm is commonly used in data encryption?
A. RSA
B. Dijkstra’s Algorithm
C. Grover’s Algorithm
D. Depth-First Search
Answer: A. RSA
11. What is SQL Injection?
A. A technique to bypass firewalls
B. Injecting malicious SQL code into a database query
C. A way to encrypt SQL queries
D. Injecting data into a secure website
Answer: B. Injecting malicious SQL code into a database query
12. Which cybersecurity tool is known for penetration testing?
A. Metasploit
B. Microsoft Excel
C. Tableau
D. AutoCAD
Answer: A. Metasploit
13. What is the function of Multi-Factor Authentication (MFA)?
A. To improve system processing speed
B. To use multiple layers of security for user authentication
C. To encrypt user passwords
D. To detect malware on a network
Answer: B. To use multiple layers of security for user authentication
14. What is the role of Intrusion Detection Systems (IDS)?
A. To prevent unauthorized access
B. To detect suspicious network activity
C. To encrypt sensitive data
D. To monitor user behavior
Answer: B. To detect suspicious network activity
15. Which type of hacker works ethically to secure systems?
A. Black Hat Hacker
B. Grey Hat Hacker
C. White Hat Hacker
D. Script Kiddie
Answer: C. White Hat Hacker
16. What is the primary purpose of GDPR?
A. To monitor hackers
B. To enhance data privacy in the European Union
C. To regulate cloud storage services
D. To encrypt public data
Answer: B. To enhance data privacy in the EU
17. Which cybersecurity principle ensures data is accurate and not tampered with?
A. Confidentiality
B. Integrity
C. Availability
D. Scalability
Answer: B. Integrity
18. What is the most common type of attack on IoT devices?
A. Ransomware
B. Brute force
C. Man-in-the-Middle (MITM)
D. Botnet attacks
Answer: D. Botnet attacks
19. What is ransomware?
A. Malware that self-replicates
B. Malware that encrypts files and demands payment to unlock them
C. Malware that spies on user activity
D. A denial-of-service attack
Answer: B. Malware that encrypts files and demands payment to unlock them
20. What is a zero-day vulnerability?
A. A vulnerability detected on the first day of system deployment
B. A flaw that is exploited before a patch is released
C. A hardware-related issue
D. A network configuration error
Answer: B. A flaw that is exploited before a patch is released
21. Which tool is commonly used for creating secure communication protocols?
A. SSL/TLS
B. SQL
C. HTML
D. CSS
Answer: A. SSL/TLS
22. What is the primary function of Kali Linux?
A. Malware analysis
B. Penetration testing and security auditing
C. Creating firewalls
D. Managing user authentication
Answer: B. Penetration testing and security auditing
23. What is social engineering in cybersecurity?
A. Using software to create secure systems
B. Manipulating people to divulge sensitive information
C. Studying the structure of social networks
D. Encrypting data for secure transmission
Answer: B. Manipulating people to divulge sensitive information
24. Which of the following is NOT a cybersecurity best practice?
A. Using strong passwords
B. Clicking on unknown links in emails
C. Enabling two-factor authentication
D. Regularly updating software
Answer: B. Clicking on unknown links in emails
25. What does HIPAA regulate?
A. Financial data security
B. Cybersecurity for IoT devices
C. Protection of health information
D. User authentication mechanisms
Answer: C. Protection of health information
